A Guide to Ransomware, Open Source and IoT


You click on a link or open an attachment, and suddenly a ransom note hovers on your screen saying that all your files have been encrypted. You frantically try to close the message and access your system files. But to no avail. It seems you have two choices. Either answer the ransom demands to decrypt your files, or you say bye-bye to your files.
In this week’s post, we’re going to explore the nefarious (and at times plain weird) story of ransomware, and how you can protect yourself from its grasps.
The Birth of Ransomware
The year is 1989 and the WHO International AIDS conference has just finished. After the event, 20,000 attendees across 90 countries receive a floppy disk labeled ‘AIDS Information – Introductory Diskettes’. Users insert the floppy into their drive to find a survey measuring a person’s risk of contracting AIDS. Nothing strange here, right? Just wait.
After 90 reboots, the ‘AIDS Trojan’ (transmitted by way of diskette to the user’s computer) suddenly activates, encrypting all of the victim’s data. A message then pops up on the user’s screens, instructing them to turn on their printer. Upon doing so they read that in order to regain access to their files, they must first send $189 to an address in Panama.
Who was behind this diabolical scheme I hear you ask. Well, a one Dr. Joseph Popp, a Harvard-educated evolutionary biologist. Not the average criminal profile it’s true, but we have Dr. Popp to thank for giving birth to today’s ransomware.
Although ransomware’s methods have changed over the years, its motivation has remained the same – extorting money by way of holding peoples’ information hostage.
Ransomware Goes Mainstream
Between 2011-2014, the yearly average of ransomware attacks hovered around the 100,000 mark. A significant problem indeed. Yet with the advent of CryptoWall 2.0 in January 2015, the number of attacks skyrocketed to 725,000 in the first quarter of 2015 alone. And since then, instances of ransomware attacks have only continued to rise.
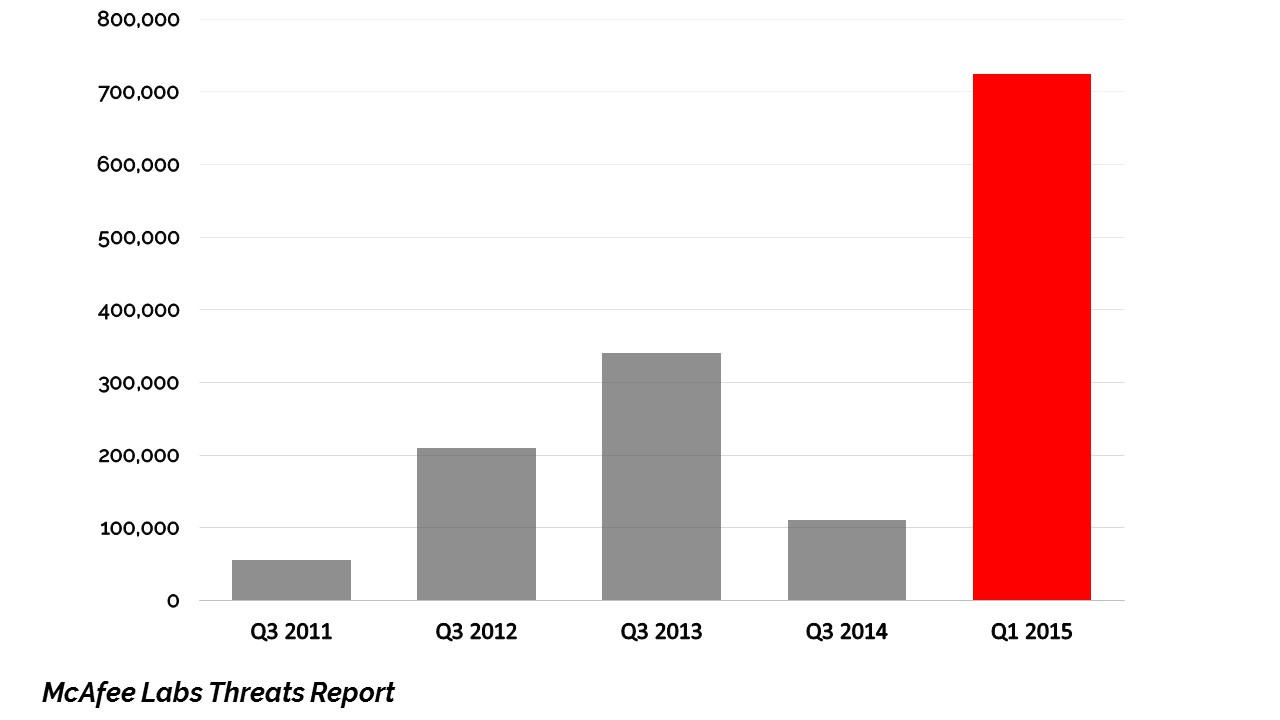
Like many of the ransomware before it, CryptoWall 2.0 encrypted user’s data and demanded a ransom for the decryption key. However, what set CryptoWall 2.0 apart from its predecessors was its professionalism and sheer sneakiness.
To begin with, CryptoWall 2.0 was the first ransomware to use its own anonymous Tor gateway to hide the location of the kidnappers. Also, the ransomware had many attack vectors, including email attachments, malicious pdf files and even exploit kits (think of them as ransomware toolkits for hire).
Not only that, CryptoWall 2.0 was a smart cookie, being able to switch its process execution context between Windows 32 and 64 bit. Meaning it could adapt itself according to the hosts operating system, therefore doing maximum damage. Finally, a spot of customer service was added to the whole affair, as each victim was given their own bit coin payment addresses, meaning no longer could a user’s ransom be stolen by another victim. Thankfully, fixes were developed, but only after CryptoWall 2.0 had put ransomware on the global radar.
Believe it or not, the next chapter in ransomware’s story comes from noble beginnings, but its ending is far more chilling.
Open Sourcing Ransomware
It all started in August 2015 with Utku Sen, a white hat hacker from Turkey. Utku Sen developed and published a piece of ransomware dubbed Hidden Tear, and published it on GitHub, in order to educate people on threats of ransomware.
Unsurprisingly, the not so ‘educationally-minded’ actors decided to use the code to target unwitting victims mainly via phishing. However, Utku Sen got wise and inserted a security flaw into the code, thus foiling would-be kidnappers. But this was not the end of ransomware’s open source journey by any stretch.
First Utku Sen developed and published the EDA2 ransomware on GitHub. This wasn’t such a big deal as once again Utku Sen inserted a backdoor to access the decryption keys. However, with Magic in January 2016, things got nasty.
Although Utku Sen wasn’t directly involved in Magic’s development, it was based on EDA2’s source code. However, when Magic’s web hosting providers deleted the criminals’ account after receiving a complaint, all of their files were also lost. Therefore, when Utku Sen tried to access his backdoor, this time he was left out in the cold. Surprisingly, the kidnappers did finally release the decryption keys, but only after Utku Sen answered their demands and took down EDA2’s source code from GitHub. All’s well that ends well, right?
The latest chapter in this saga occurred in June this year when Ded Cryptor burst onto the scene.

Ded Cryptor is a true child of open source, borrowing its code from many sources. It uses EDA2’s source code, and borrows its code for its proxy server and sending requests from two different sources. Worryingly, its method of distribution is still unknown, but there are fixes out there.
In the final part of our story, ransomware, open source and IoT join forces.
Ransomware and IoT – A Glimpse of Things to Come?
At August 2016’s DEF CON, 2 UK researchers demonstrated the world’s first ransomware targeting IoT devices – in this case a nest thermostat.

Obviously, there are no files or data to block access to. So what does the ransomware do exactly? Take control of the thermostat itself. This might not sound worrying at first, but as the program raises the temperature to 99 degrees, and demands a 1 bitcoin ransom every 30 seconds, this is surely something to sweat about.
The thermostat in question is basically a Linux computer, and so the ransomware exploits an open source component vulnerability to take control. To date, a patch hasn’t been released, as the researchers are currently in touch with the manufacturers developing a fix.
As the method of distribution is by way of an SD card, the risk of infection is considerably low. However, with ransomware making its first IoT appearance, could this be a sign of things to come?
Prevention is Better than Cure
So, with all of this nasty ransomware out there, what you can you do to protect yourself?
The first step is to back-up your data regularly, and store it offline to avoid attackers getting their grubby little hands on it. Therefore, if you are attacked, you can always restore your system to an earlier state.
Another great tip is to educate your enterprise on internet best practices. As the most popular methods of infection are email phishing attacks (where a user is spammed with emails containing a dodgy attachment or link) and malvertising (where malware is embedded in ads), employees should be trained to always scan attachments before downloading, avoid clicking on suspect URLs and use such tools as AdBlock to block malicious ads.
Finally, as ransomware often exploits known vulnerabilities in outdated software , you should always keep your commercial and third-party versions up-to-date. This is pretty straightforward in regards to commercial software, as you can rely on the vendor issuing its customers with the latest security updates. Yet, with third-party software, especially open source, things can be a bit trickier.
As you’re responsible for tracking your open source usage, you must also keep an eye out for security vulnerabilities detected by the open source community, and their patches/fixes. If you don’t, you risk falling prey to hackers out there. For if the community knows about a security vulnerability, so do they.
