Are You Using One of the Top 6 Most Vulnerable Open Source Projects?


We already know that most if not all enterprises and organizations rely on open source software to develop their offerings. As organizations continuously extend their open source usage, we decided to look at our data to learn more about the most popular open source projects.
Our research team analyzed our database, which includes over 3M open source components and 70M source files, covering over 20 programming languages, to learn: which are the most popular open source projects currently in use and how safe are they?
This is what we found:
Let’s take a closer look at the popular open source projects found to be most vulnerable:
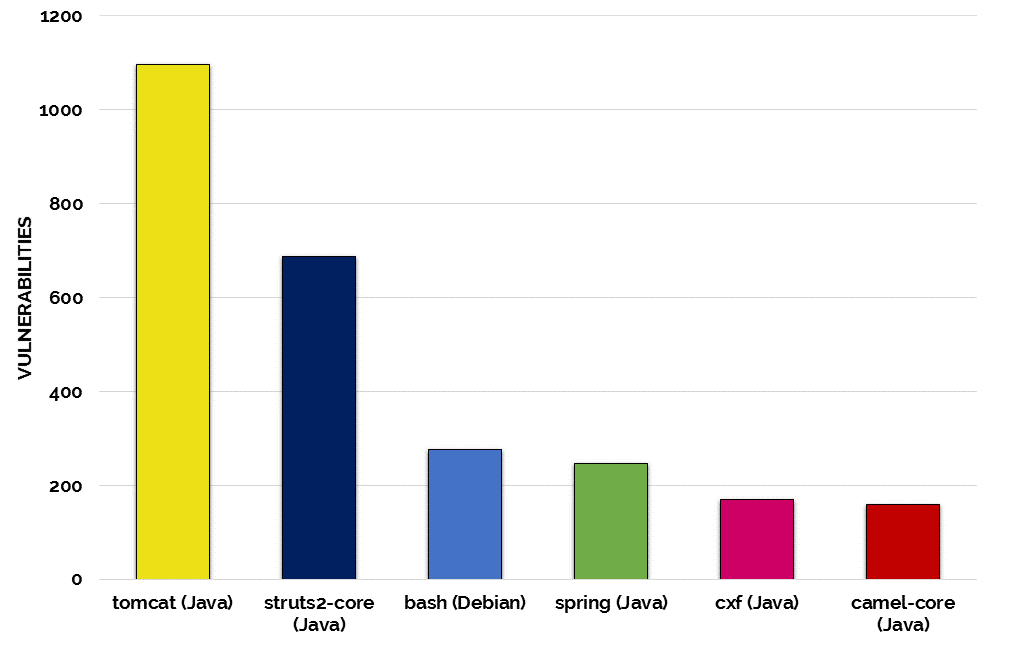
This open source web server takes the dubious title of the most vulnerable open source project, Apache Tomcat came in with 1096 known vulnerabilities. Specifically, this number includes Tomcat-Catalina – Tomcat’s servlet container, with 836 vulnerabilities, and Tomcat-Coyote – a connector component, with 260 vulnerabilities.
#2 struts2
Second in our most vulnerable list with 687 vulnerabilities, struts2 is one of the most popular frameworks for developing web applications in Java, due to its flexibility and extendibility.
Some of you may remember that just last month a vulnerable upload functionality in this open source project was exploited.
#3 Bash – 276 vulnerabilities
Bash is the shell, or command language interpreter, for the GNU operating system that offers functional improvements over sh for both interactive and programming use. Bash is portable and currently runs on nearly every version of Unix and a few other operating systems.
Though 276 is quite an impressive number, Bash has had one vulnerability that that still haunts the development community: I’m referring, of course, to the notorious Shellshock bug.
#4 Spring – 247 vulnerabilities
Spring is one of the most popular Java application development frameworks because of its modularity and lightweight. It incorporates layering, a lightweight container, and the ability to program on an interface.
#5 CXF – 169 vulnerabilities
Apache CXF is a framework for developing Web Services and front end interface communication, from small JSON utilities for web applications to a full-scale enterprise service bus (ESB). CXF includes a broad feature set, but it is primarily focused on Web Services Standards Support, Frontends, Ease of use and Binary and Legacy Protocol Support.
And, last but not least:
#6 Camel – 160 vulnerabilities
Apache Camel is an open source integration framework based on known Enterprise Integration Patterns (EIPs), that provides a standardized, internal domain-specific language (DSL) to integrate applications.
Java Here, Java There
One of the first things that jumped out at me when reviewing this list was that five out of the six most vulnerable projects run on Java, and four out of those are development frameworks. Why are these projects so popular?
Experts recommend Open-source Java frameworks as a great way to jump-start application development and boost developer productivity, ultimately supporting better coding standards and helping to eliminate bugs.
Data from GitHub also reflects the rising predominance of Java projects, citing the popularity of Android, which uses Java as a primary language for building apps for phones and tablets, as well as the increasing demand for version control platforms at businesses and enterprises, as a possible stimulus to this growth.
Why Is Everyone Using Java-based Projects If They Are So Exploit-friendly?
While the continuous rise of Java in open source projects is impressive, I can’t help but wonder: what about all these vulnerabilities? Clearly, these open source projects are less secure and easier for hackers to exploit, so why are so many organizations using them? Why is the open source community promoting them? Shouldn’t we work to avoid the open source Java components and replace them with safer proprietary or third party code?
The high number of vulnerabilities did, in fact, make my head spin. But – it’s not as simple as that. Open source projects do not contain more defects or vulnerabilities than proprietary ones. Both are patched and updated frequently.
The difference with these Java open source projects – and many other popular open source components, is that they are managed and supported by a dedicated open source community of experts. The fact that the open source vulnerabilities, as well as their fixes and updated versions, are well documented is a testament to that. While the security updates about the paid solutions that you are using come to you from vendors, the information about these popular open source projects is shared and published by the community for all users, frequently updated as new information and solutions are discovered.
One of the reasons developers made these top 6 open source projects so popular is because the support base is so reliable. So, the short answer is: keep making use of these open source resources. They are more likely to help you avoid and remediate critical vulnerabilities than leave you compromised.
Open Source Vulnerability Management
If you want to sleep peacefully at night, not to mention keep your security officers happy, it is important that you make sure you manage the security of your open source projects. Many development teams don’t even know the extent of the open source projects that they are using. Don’t be one of those teams. There are quick and reliable ways to monitor your open source components. Stay alert and updated regarding code updates and fixes. These open source security vulnerabilities shouldn’t be scary at all – as long as your survival kit is properly assembled.