What is Software Composition Analysis (SCA)?

Open source code is everywhere, and it needs to be managed to mitigate security risks.
Developers are tasked with creating engaging and reliable applications faster than ever. To achieve this, they rely heavily on open source code to quickly add functionality to their proprietary software. With open source code making up an estimated 60-80% of proprietary applications’ code bases, managing it has become critical to reducing an organization’s security risk.
Software Composition Analysis tools help manage open source use.
What is software composition analysis?
Software Composition Analysis (SCA) is a segment of the application security testing (AST) tool market that deals with managing open source component use. SCA tools perform automated scans of an application’s code base, including related artifacts such as containers and registries, to identify all open source components, their license compliance data, and any security vulnerabilities. In addition to providing visibility into open source use, some SCA tools also help fix open source vulnerabilities through prioritization and automated remediation.
Inventory
Software Composition Analysis tools typically start with a scan to generate an inventory report of all the open source components, (dependecies) in your products, including all direct and transitive dependencies. Having a detailed inventory of all your open source components is the foundation of managing your open source use. After all, you cannot secure or ensure compliance of a component you don’t know you’re using.
License compliance
Once all open source components have been identified, SCA tools provide information on each component. This includes details about a component’s open source license, attribution requirements, and whether that license is compatible with your organization’s policies.
Security vulnerabilities
One of the main functions of Software Composition Analysis tools is to identify open source components with known vulnerabilities. Good software composition analysis solutions will not only tell you what open source libraries have known vulnerabilities, but they will also tell you whether your code calls the affected library and suggest a fix when applicable. The solution should also identify open source libraries in your code base that need to be updated or patched.
Types of vulnerabilities that can be found using SCA
Open source vulnerabilities typically occur when there are flaws or weaknesses in the code. These may be unplanned coding errors or inconsistencies that have been deliberately inserted into the code. Attackers can then exploit them to gain unauthorized access to systems, steal data, or cause damage to the software or system. Vulnerabilities can also result from old software or versions of current software that hasn’t been updated. These can cause security vulnerabilities that attackers can use to infiltrate your code and exfiltrate sensitive and valuable data, which can be disabled and ransomed, for example.
SCA can also help identify licensing risks to ensure license compliance with any third-party code being used.
Advanced Software Composition Analysis (SCA) features
Advanced SCA solutions also include automatic policy enforcement, which cross-references every open source component found in your code with organizational policies and triggers different responses, such as initiating an automated approval workflow or failing the build.
Advanced SCA solutions automate the entire process of open source selection, approval, and tracking. Some are even able to alert developers about vulnerabilities in a component before a pull request is made and the component enters the system. This saves developers precious time and increases their accuracy.
Limitations of Software Composition Analysis (SCA)
SCA focuses on identifying and remediating risks in open source components and third-party dependencies. It is not designed to find vulnerabilities in custom (original) code. For example, the SolarWinds supply chain breach wasn’t something that could have been alleviated by SCA, because SolarWinds’s source code is proprietary. To scan and remediate proprietary code, use SAST (static application security testing). SCA also doesn’t detect insecure network configurations.
Older SCA solutions weren’t designed to scan development and deployment environments, so they cannot secure the later parts of your software development lifecycle (SDLC). And some older SCA tools don’t provide the context needed to accurately assess the risk impact of any issues. Without this context, these tools can generate too many false positives, which consumes limited resources as security teams end up making unnecessary fixes. Note: Newer, more modern SCA solutions have addressed this challenge with prioritization capabilities, so make sure to choose a solution that can do this (see “Prioritization and remediation,” below).
The evolution of software composition analysis
The first open source manual scanner was released around 2002. Despite greater visibility into organizations’ code bases, this early technology resulted in a high rate of false positives, which required manual intervention and did not meet the needs of agile development environments.
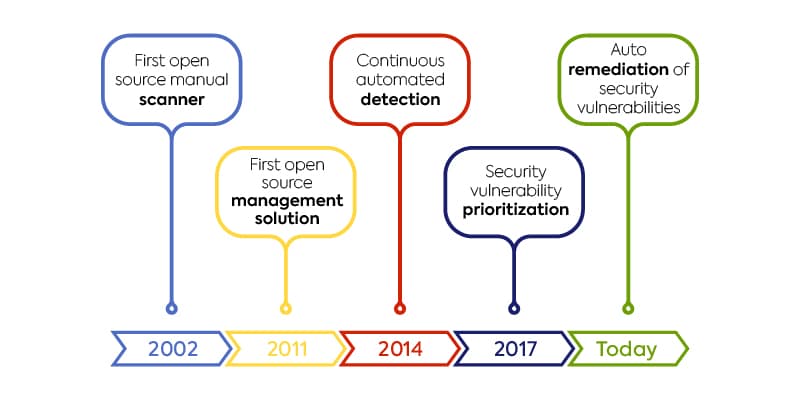
By 2011, the technology had improved was capable of automatically detecting vulnerabilities and licensing issues in real time. This enabled software and security teams to deploy open source management earlier in the development cycle. At the same time, SCA solutions were also being integrated with software development tools like repositories, build tools, package managers, and CI servers, which put the power of open source management and security in developers’ hands. Despite these advancements, SCA still heavily focused on detection.
The impact of emerging technologies on SCA
More and more source code, components, and dependencies are being used to create new software and applications. It is widely estimated that as much as 90 percent of some organizations’ source code is now open source, which means that the potential attack surface has expanded considerably and continues to do so. This increases the risk of open source vulnerabilities and the threat of malicious packages infiltrating and attacking software and applications. So, the need for SCA increases in importance.
The future of SCA in software development
Developers, DevOps, and DevSecOps teams are now being tasked with scanning, identifying, and remediating vulnerabilities in open source far earlier in the SDLC. They are shifting security left to address and fix issues sooner rather than waiting until the software is ready for production or shipping. There is an even newer trend in the development process, known as “shifting smart”, which encourages teams to adopt nimble scanning and remediation processes that quickly and easily fix code wherever it is in the SDLC, and do so within existing developer workflows. Modern SCA solutions can do this, as well as prioritize vulnerabilities and identify those that can be safely ignored. This puts modern SCA at the heart of any robust application security strategy.
Detection Is Not Enough
As open source use continues to proliferate, the number of known open source vulnerabilities has also increased. When you take into account the volume of alerts developers and security professionals deal with daily, it all starts to become noise.
Focusing solely on detection is only the first step. It does not help organizations reduce their risk. Detection without remedy is an incomplete application security model.
So how do you forge ahead? To address today’s threat landscape, you don’t need to strive for perfection, but you do need to keep moving forward. To do so, organizations must adopt a mature SCA security model that includes prioritization and remediation on top of detection so developers and security professionals can focus on what really matters.
Prioritization and Remediation
Modern SCA solutions now bridge the gap between detection and remediation.
Prioritization. A mature software composition analysis tool should include technologies that prioritize open source vulnerabilities. By automatically identifying the security vulnerabilities that present the biggest risk, organizations can address these priorities first. Developers and security professionals don’t waste their time and resources sifting through pages of alerts trying to determine what vulnerabilities are the most important, possibly leaving highly exploitable vulnerabilities running in a production system.
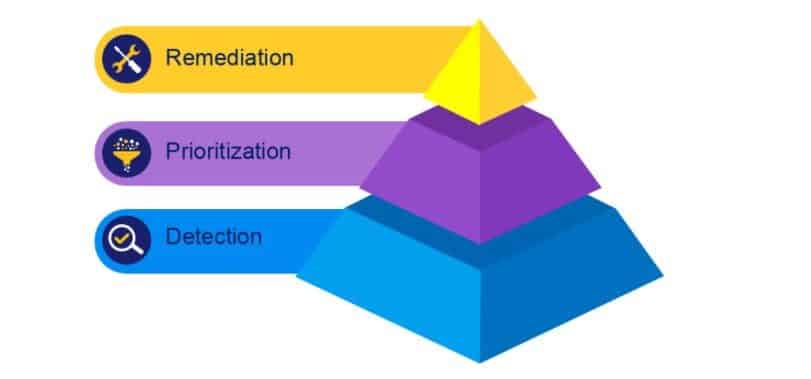
Remediation. After prioritization comes remediation. Remediating vulnerabilities automatically goes beyond just showing developers where the vulnerability is located to suggesting a fix and providing data on how likely the fix will impact a build. Automated remediation workflows can be initiated based on security vulnerability policies triggered by vulnerability detection, vulnerability severity, CVSS score, or when an updated version is released. One of the most reliable risk mitigation strategies is to keep your open source components continuously patched to avoid being exposed to known vulnerabilities. A good SCA solution helps you achieve this.
Advanced SCA tools – including repo, browser, and IDE integrations – seamlessly integrate into the software development life cycle (SDLC) to resolve vulnerabilities early when they are easier and cheaper to fix.
Software Composition Analysis requirements
Comprehensive Database
The database is the heart of any SCA solution. The more comprehensive the database, aggregating data from multiple sources, the better it is at identifying open source components and security vulnerabilities. Without a comprehensive, continuously updated database, you would be unable to detect the right versions of open source components to update licenses, remediate security vulnerabilities, and apply updates and patches. The open source community is highly decentralized. Because there is no one centralized source of information on updates or patches, you rely on the database for everything.
Broad Language Support
An SCA solution should support not only the languages you are currently using but any language you might be considering using within the next year or two. You wouldn’t want to implement an SCA solution only to find it doesn’t support the language of your newest project a year from now. Plan ahead and choose a solution with broad language support.
Extensive Reporting
From inventory, licensing, attribution, and due diligence reports to vulnerabilities and high-severity bug reports, you need a solution that offers a wide range of reporting tools tailored to every use case, including management, legal, security, DevOps and DevSecOps.
Robust Policies
Choose a solution with automated policies that are robust yet highly flexible and customizable so you can define your organization’s own unique needs. Policies that automate the process of open source selection, approval, tracking, and remediation save developers time and greatly increase their accuracy.
Vulnerability Prioritization and Remediation
As discussed earlier, you need a solution that prioritizes security vulnerabilities and offers remediation advice. The more you automate, the easier it will be to resolve the most critical issues first without slowing down development.
Dual Governance and Developer Focus
SCA solutions fall into two broad categories.
Governance solutions, used by management, security, DevOps, and legal teams, provide full visibility and control across an organization’s software portfolio.
Developer tools help developers avoid vulnerable open source components before a pull is made and fix any vulnerabilities detected in their code via tools integrated with native development environments.
The best SCA solutions offer both governance and developer tools. This guarantees that everyone gets the tools they need, when and where they need them.
Integration with DevOps Pipeline
Choose an SCA solution that integrates seamlessly with a wide range of developer environments at every stage of the SDLC – repositories, build tools, package managers, and CI servers – so developers can decide whether they can or should use an open source component before a pull request is made.
Containers/Kubernetes
Container and Kubernetes use is widespread, yet security remains a challenge. Select an SCA solution that scans open source components from inside your containerized environments, identifying vulnerabilities or compliance issues and automatically enforcing policies. Also, make sure the solution has native support for your specific container registry.
Why SCA should be part of your application security portfolio
Open source components have become the main building block in software applications across all verticals. Yet despite the heavy reliance on open source, too many organizations are lax about ensuring that their open source components meet basic security standards and are compliant with licensing requirements.
Securing your application in today’s complex digital world is a challenge. With the right Software Composition Analysis solution, you are one step closer to mitigating your open source risk.
Overview of regulatory compliance requirements
Regulatory compliance is growing in importance as organizations working on M&A activity or with government bodies are frequently required to demonstrate that their software is secure and legally compliant with license conditions.
Governments are now taking a more active role in this arena by introducing new cybersecurity strategies that companies must follow.
Having issued an Executive Order on improving the nation’s cybersecurity, and having passed the Strengthening American Cybersecurity Act, the U.S. Government announced the release of its national cybersecurity strategy in 2023. Similarly, the European Union announced its Digital Operational Resilience Act (DORA) and its Cyber Resilience Act (CRA) to enforce software security and secure delivery of services.
The Australian government has stated its aim to make Australia the most cyber-secure nation in the world by 2030. And in concert with these developments, agencies from Australia, Canada, Germany, The Netherlands, New Zealand, the United Kingdom, and the United States have together created a guide for software development organizations to ensure their products are both secure by design and by default.
These recommendations and strategies require more accountability from vendors, increased visibility into their code bases, software, application components, and dependencies, and tougher regulatory compliance.
How SCA can help with compliance
SCA is focused on scanning, detecting, and remediating vulnerabilities in open source, which can include identifying and fixing components and dependencies that do not meet license requirements. By finding such issues and versions that comply with license conditions, SCA can help ensure that your code base is up-to-date and fully compliant.
Case studies of SCA in compliance
Educational technology company Learning Pool sought a further round of VC investment and its preferred investor was particularly concerned about the company’s use of open source software. They wanted assurances that Learning Pool had policies written and a process in place to safeguard its codebase from legal challenges. Learning Pool uses Mend SCA to scan code and identify if any components aren’t compliant. Compliant code is automatically built and deployed. Mend SCA alerts Learning Pool to non-compliant code and blocks it. Everything is done speedily and automatically.
Workvision uses open source software to improve quality and speed in development and to reduce costs. It needs to ensure that this software is used in compliance with the relevant licenses. Before using Mend SCA, the company found it difficult to carry out regular audits of its open source use and often completed these audits in the final stages of development, which led to delay development. Mend SCA has accelerated the process of identifying and fixing any compliance issues, Prior to using Mend SCA, completing an open source audit took about a week to complete. Now it can take as little as 15 minutes.
The Fintech Open Source Foundation (FINOS) accelerates collaboration and innovation in financial services through the adoption of open source software, standards, and best practices. FINOS invested heavily in building its Open Developer Platform (ODP), but FINOS’s members needed to be confident their open source components had no known vulnerabilities and were compliant with license policies. Mend SCA manages the open source licenses and security vulnerabilities in FINOS’s open source projects. With Mend SCA, FINOS can create policies around license compliance, security vulnerabilities, and quality issues that are automatically enforced. This ensures that all committed code meets FINOS’s high standards of code quality, without impeding the speed of the development process.
These are just three of many examples of how SCA can improve and accelerate license compliance.
Benefits of Software Composition Analysis
- Improved security. SCA’s specific purpose is to scan your open source software, components, and dependencies, identify vulnerabilities, and with a modern SCA tool, automatically remediate these vulnerabilities. When using these capabilities to their fullest, SCA will certainly improve your application security.
- Cost savings. Identifying and remediating open source vulnerabilities requires considerable resources when done manually, and missing vulnerabilities can adversely affect the speed of development and innovation. This is costly. SCA accelerates and automates the process, lightening the load for developers and DevOps teams and making security cheaper to implement and more thorough.
- Enhanced efficiency. Modern SCA tools are specifically built to accelerate and automate the detection and remediation process. So, they make the process easier and faster. Plus, their ability to prioritize vulnerabilities to be addressed means that false positive results are significantly reduced, and teams spend far less time fixing issues that aren’t relevant.
- Improved developer productivity. Speed, efficiency, and automation liberate developers from the time-consuming task of scanning and securing open source. They can now do it more efficiently than ever, and the process is seamless when it is done within their development workflow, thereby minimizing any interruption to their innovation pipeline. With SCA, developers can be sure that the security of their code base is robust while enabling them to maintain and increase their productivity.
FAQs
SCA is only suitable for open source. You need SAST to scan and remediate proprietary code. And traditional SCA can generate a large number of false positives.
You should choose an SCA tool that meets your needs whilst being as simple to use and unintrusive as possible. Ensure that your choice of tool is developer-friendly. It should ideally work within their existing workflows so they don’t have to exit their development environment to implement security functions, and it shouldn’t require them to learn a whole new software. To that end, it should seamlessly integrate into existing software and development environments.
Your SCA tool should do more than simply scan; it should provide a thorough analysis of software components and their dependencies. It should be able to prioritize the riskier vulnerabilities that need your attention within your particular projects and scope of work. It should serve up clear, comprehensive reporting that will form the bedrock of high-quality governance and control, and it should be able to remediate vulnerabilities quickly and easily. Ideally, this process will be automated and scalable so that your SCA capabilities will grow as your code base and your range of software and applications expands. And it should now be cloud native.
Software composition analysis is becoming increasingly vital as a security and governance tool, because more and more software and applications are being developed with open source components. It is also increasingly clear that shifting security left and shifting it smartly will be necessary to reinforce application security and maximize its efficiency. SCA is essential to making this happen.
